I have developed in the past month or so a way to have position-independent-code (PIC) firmware image (on ARM Cortex-M0 and Cortex-M4) which can be put (almost) anywhere in flash. I’m still refining the concept and will write an in-depth-article about it. There is a part of the PIC stuff that I can discuss briefly to get us going about THIS article.
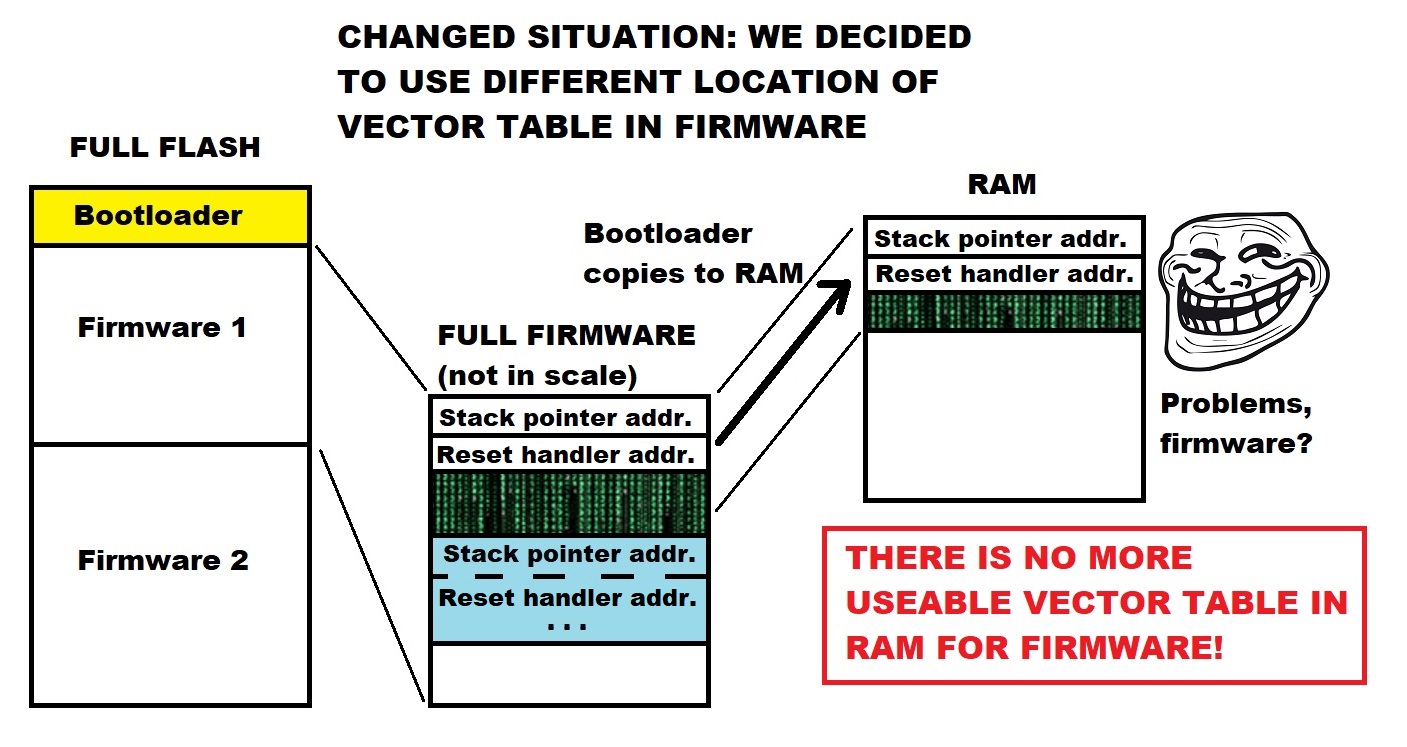
Part of the PIC firmware + bootloader has been interrupt vector table relocation. Basically the bootloader needs to read from flash the firmware vector table and copy it to RAM and then point the MCU to use the vector table from RAM. Some of tutorials, videos and comments suggest that bootloader should do the relocation. I have, however, come to the conclusion that this is actually wrong way to proceed. I will try to demonstrate now why.
Continue reading “Firmware interrupt vector table relocation by bootloader considered harmful”