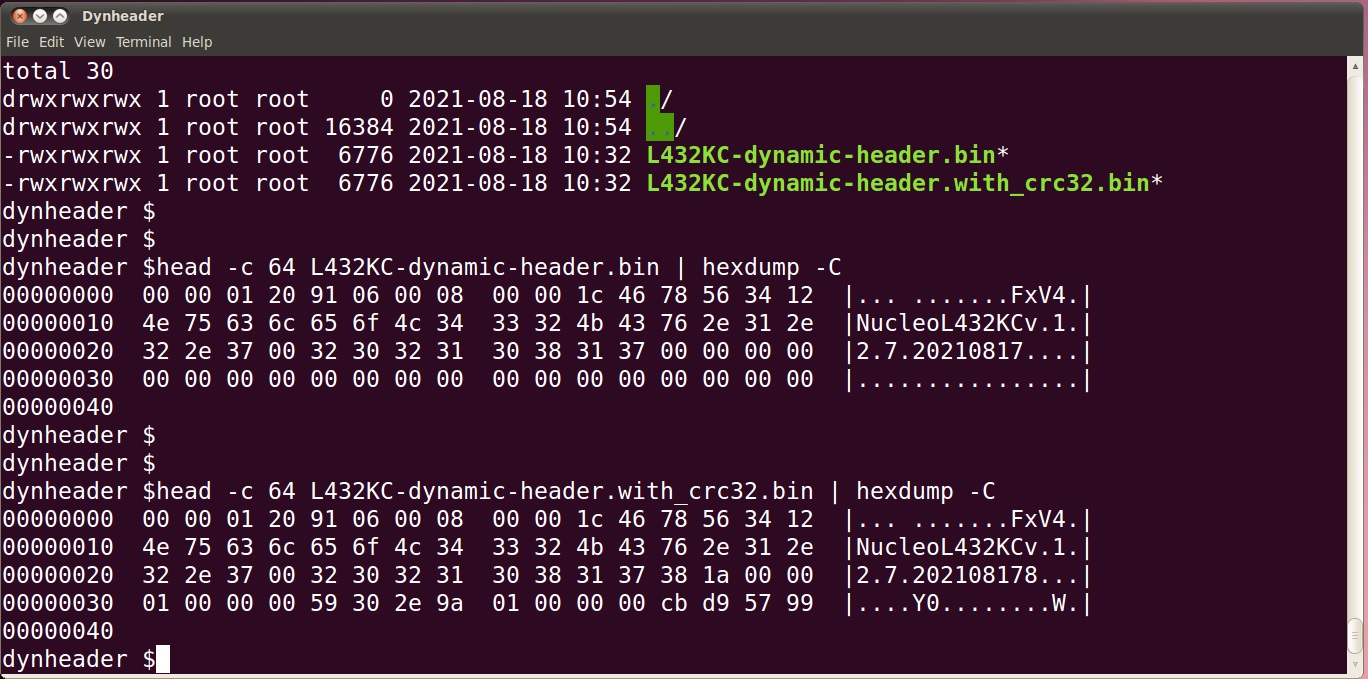
Every seasoned embedded systems engineer faces at some point of their career a problem about needing to put a header to their built firmware image binaries. This header usually contains at least information about what device the image is for and what version number the image is. Checksums are also common.
There are multiple ways of implementing the header. One solution is to just glue it on top of the image and peel it off while updating the firmware via IAP or external programmer means.
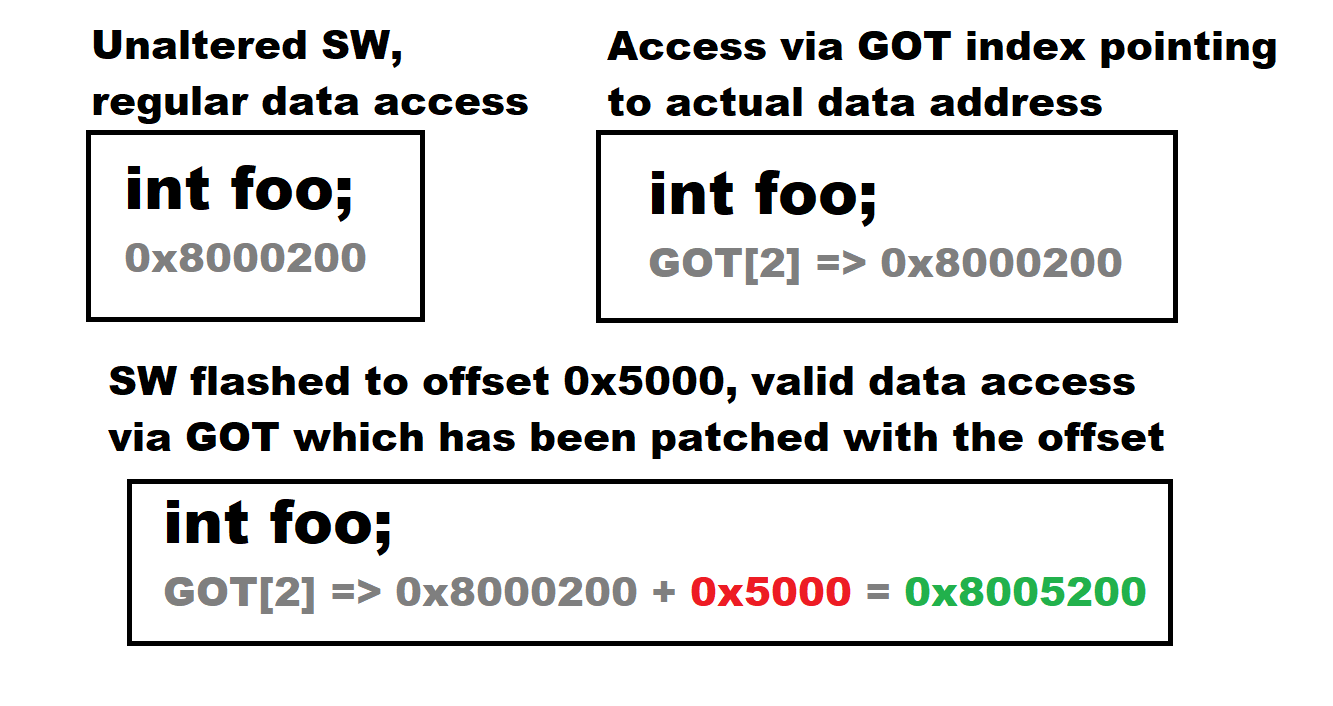
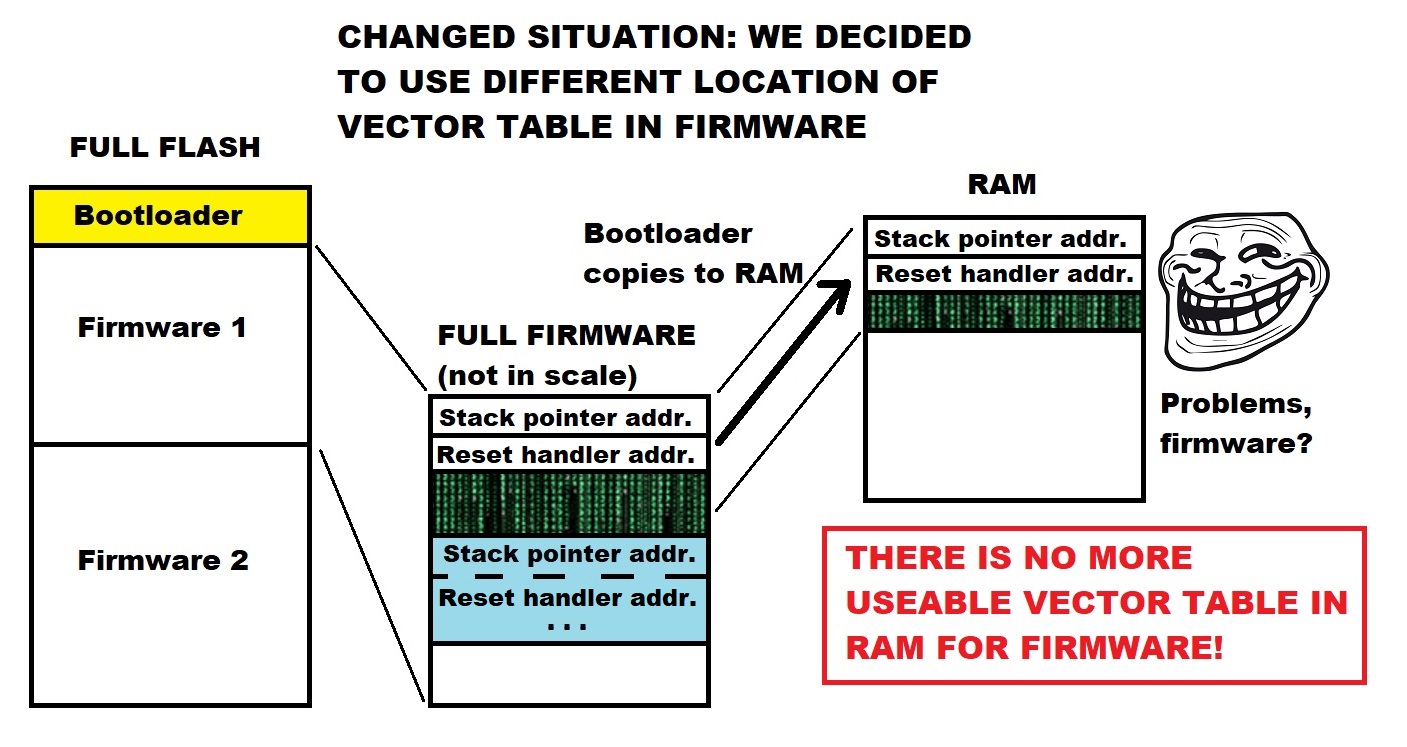
Another approach is to place it actually in firmware flash, to a known location, possibly even start of the image, but use a bootloader to jump past the header.
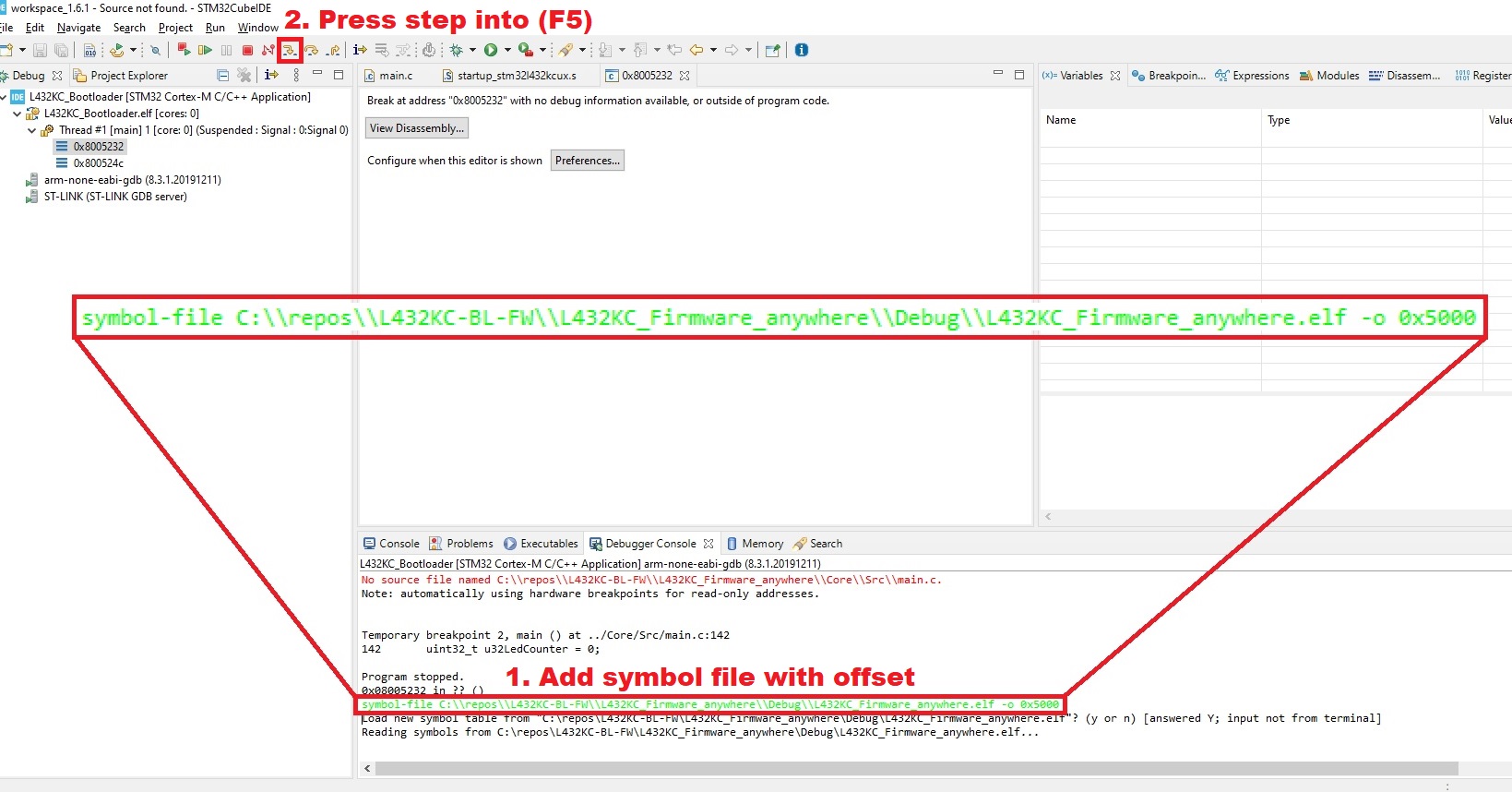
There is however yet another solution I’m going to demonstrate. It is about generating the header template directly into the flash image, and even surprisingly in a way that the MCU can start executing actually from the beginning of the header (template). An external tool is used later to fill in checksum data.
But before continuing, heres a big fat warning:
WE ARE MANIPULATING VECTOR TABLE OFFSETS WHICH IS CONSIDERED DANGEROUS PRACTICE REGARDING ULTIMATE RELIABILITY OF THE RUNNING CODE. YOU HAVE BEEN WARNED.
There. Now lets go on.
We will be working on our trusty old STM32 Nucleo-L432KC and STM32CubeIDE. Example codes are available at https://github.com/usvi/L432KC-dynamic-header .
Continue reading “Dynamically generated MCU binary image header (Arm Cortex-M4)”